Latest Fraud Alerts for Business
When it comes to protecting your business from fraud and cybercrime, it pays to know the latest threats. That's why NBT Bank is committed to providing you with the most up-to-date information and alerts. Click the headings below to learn more about recent scams and tactics being used by cyber criminals.
Check fraud continues to be a popular avenue for fraud and account numbers can easily be obtained by fraudsters by intercepting both incoming and outgoing mail from mailboxes.
One example of fraud with intercepted mail occurs when criminals go “fishing”, a method in which they will attach something sticky to a weighted object tied to a string, drop it in the mailbox and pull in whatever they can get.
If the envelope contains a check, the thief will alter it by erasing the ink using household chemicals. The check will then be rewritten to a different person, usually for a significant amount and cashed in at an ATM or financial institution. Another common practice is to sell the altered check on the dark web, or in another part of the country.
To minimize stolen check fraud, the banking industry suggests you take the following precautions:
- Use a pen with indelible black gel ink that can’t be erased.
- Deposit mail with checks inside the post office, not in outdoor blue mailboxes
- If you choose to leave outgoing mail in your mailbox, don’t put up the flag.
- Grab incoming mail right away.
- Deposit mail with checks just before a mailbox’s last pickup.
- Pay your bills online.
- Talk to your NBT relationship manager about check fraud prevention tools that can be added to your account
- Keep an eye on your bank accounts for potential fraud, and report suspicious activity as soon as possible.
As a valued customer of NBT Bank, we want to provide you with a brief, proactive assessment of potential cyber risks related to the Ukraine-Russia conflict as well as resources to address those risks. As your chosen financial services provider, we want you to know that NBT is prepared and our defenses are strong. Below are some important risks and resources to assist you and your business.
Risks to Consider
All US businesses, particularly critical infrastructure, are subject to the general threat of retaliation by Russia at this point, namely due to US support of Ukraine and sanctions the US has imposed against Russia.
- What to do: Follow CISA's Shields-Up guidance, which outlines general cybersecurity practices that will help your business resiliency in the event of a cyber-attack.
- Resource: https://www.cisa.gov/shields-up
Businesses could also be subject to a general increase in ransomware risk resulting from the severing of diplomatic ties between Russia and the US.
- What to do: Follow CISA's recommended practices to detect, defend and respond to potential ransomware attacks.
- Resource: https://www.cisa.gov/stopransomware/ransomware-guide
- TIP: Your third-party service providers are subject to the same risks. Know how they interact with your systems, monitor vendor access to your network and ensure they maintain cybersecurity programs that are in line with your risk tolerance.
Small Business with limited resources?
Here are 4 things you can do to keep yourself cyber safe
General Resources
- CISA Cyber Resource Hub: https://www.cisa.gov/cyber-resource-hub
- CISA Services Catalog: https://www.cisa.gov/publication/cisa-services-catalog
- CISA - Russia Cyber Threat Overview and Advisories: https://www.cisa.gov/uscert/russia
- CISA - Mitigating Russian Cyber Threats: https://www.cisa.gov/uscert/ncas/alerts/aa22-011a
Watch out for Small Business Administration (SBA) Scams!
Phone scams, Business Email Compromise, and Check Fraud are common ‘vectors of choice’ for fraudsters, and these scams are now being used to take advantage of business customers during the COVID-19 Pandemic. These scams are dubbed coronavirus scams or ‘Small Business Administration (SBA) loan scams.’ These scams target victims, often those who received SBA Payroll Protection Program (PPP) Loans, with scammers seeking to obtain personal identifiable information (often called PII). Once they have your PII, they may attempt to access your bank account or other related cyber threats.
It is important to never give out any personal information about your financial accounts or loans to anyone other than your trusted banker.
Please note that NBT Bank has not contracted with any third parties to reach out to individuals or businesses to collect information regarding stimulus payments, SBA PPP Loan Forgiveness or the SBA’s Economic Injury Disaster Loan Program.
Please note that NBT Bank has not contracted with any third parties to reach out to individuals or businesses to collect information regarding stimulus payments, SBA PPP Loan Forgiveness or the SBA’s Economic Injury Disaster Loan Program.
Examples of SBA loan scams may include:
- Offers to process an SBA loan for you;
- Phishing attacks utilizing the SBA logo;
- Impersonating callers or spoofed emails posing as a lender or financial institution and request the routing number, account number, or credit card number that you want to use to deposit your stimulus payment;
- Emails about SBA loans that do not originate from SBA sites.
- NBT Bank will only send emails from the below email addresses in relation to SBA loans (NBTCares4Biz, NBTPayrollProtection, ESFSCMConfigurator@Fiserv.com, no-reply@nbtbankcommunications.com)
These scenarios may be attempts to obtain your private information or that of your business for nefarious purposes. If you have provided any personal or financial information please contact NBT Bank at 1-800-NBT-BANK or at reportfraud@nbtbank.com.
If you suspect an email is associated with a fraud scam targeting the SBA, report it to the Office of Inspector General’s Hotline at 800-767-0385 or online at https://www.sba.gov/COVIDfraudalert.
Recently there has been an increase in fraudulent attempts where imposters are filing for unemployment benefits using the names and personal information of people who have not filed claims.
All 50 states are reporting an increase in fraudulent unemployment benefit attempts. Threat actors are using stolen credentials to apply for benefits in someone’s name. Victim’s typically have no idea the scam is happening until they receive a notice in the mail from the state unemployment office alerting them of the claim or in some cases a debit card is received in the mail.
How are they getting this information?
Fraudsters are gathering pieces of information on the dark web from numerous data breaches that have occurred over the years. Most states only require a social security number and a date of birth to start an unemployment claim. More than 4,500 data breaches have been made public since 2015. A total of over 816 million individual records have been breached. This information can be sold and used to try and steal identities.
What should I do if I have received a notification?
If you are alerted your information was used for a fraudulent claim, follow these simple steps:
- Report the attempt to your employer.
- Contact NBT Bank immediately by email at reportfraud@nbtbank.com and/or your primary financial institution.
- Change any passwords that have been reused or not changed in the last 90 days. Keeping your financial and online baking passwords separate from email or social media sites is key!
- Visit www.identitytheft.gov to report the fraud attempt to the FTC and get help with recovery steps. They will also assist in adding a fraud alert on your credit report.
- Review your credit report often. You are entitled to a free credit report and review the information for any incorrect information. Up until April 2021, you are eligible to one free credit report weekly. You can visit www.annualcreditreport.com.
- Contact the unemployment agency in the state where the claim was filed to notify the claim was fraudulent.
a. Note: You may not be able to speak to a live representative due to the influx of calls, but it is still important to notify them via their website or an automated hotline. The full list of agencies in NBT Bank’s footprint are located below.
- Check to see if you have been exposed on any recent compromises or data breaches. www.haveibeenpwned.com
- Consider filing a report with your local law enforcement agency of the fraudulent attempt. Get a copy of that report that you can provide to creditors or credit agencies if you fall victim to further identity theft attempts.
New York
Web: https://www.labor.ny.gov/agencyinfo/uifraud.shtm
Phone: 888-598-2077
Pennsylvania
Web: https://www.uc.pa.gov/Pages/default.aspx
Phone: 800-692-7469
Maine
Web: https://www.maine.gov/unemployment/fraud/
Phone: 800-593-7660
Massachusetts
Web: https://www.mass.gov/info-details/report-unemployment-benefits-fraud
Phone: 877-626-6800
New Hampshire
Web: https://www.nhes.nh.gov
Phone: 800-852-3400 ext. 84016
Vermont
Web: https://labor.vermont.gov/form/report-ui-fraud
Phone: 877-214-3332
Connecticut
Web: https://www.ctdol.state.ct.us
Phone: 800-894-3490
Join us in celebrating National Cybersecurity Awareness Month and help promote safe online practices! Here at NBT Bank, we prioritize the safety of our customers by constantly enhancing our security measures and educating customers on how to #BeCyberSmart.
This month, we’ve joined the National Cyber Security Alliance (NCSA) and the Cyber Security and Infrastructure Agency (CISA) in their campaign to “Do Your Part.” These three simple tips encompass all necessary actions to fight against cybercrime. The focus to “Do Your Part. #BeCyberSmart” is to be intentional with your online activity.
Each week we'll be diving deeper into these topics:
If you connect it, protect it: The line between our online and offline lives is increasingly becoming blurred. Keep track of the information you’re sharing online and what rights those platforms have to it. Regularly maintain privacy settings and manage your information.
Securing devices at home & work: Now more than ever, we must protect the devices we have connected for personal and professional use. Establish unique passwords and keep them private. Set up multi-factor authentication when available and never write down your login credentials. Ensure that you’re the sole person that can login to your accounts.
The future of connected devices: With technology consistently changing and evolving, future technological improvements will affect the security of our devices. No matter what change is to come, every user needs to be prepared to #BeCyberSmart. Staying informed on the changes will help you to be prepared for any threats that may come to your personal information.
October may be dedicated to raising cyber security awareness, but the effort does not stop there. We encourage you to explore the Fraud Information Center to learn more about how to prevent, protect, and report all suspicious banking activity. This information is updated on a regular basis. Throughout the month you can also join us on Instagram, Facebook, and LinkedIn as we share information about this topic. If you believe you are a victim of fraud, notify us by emailing ReportFraud@nbtbank.com.
The Office of Inspector General recognizes that we are facing unprecedented times and is alerting the public about potential fraud schemes related to economic stimulus programs offered by the U.S. Small Business Administration (SBA) in response to the Novel Coronavirus Pandemic (COVID-19). The Coronavirus Aid, Relief, and Economic Security Act (CARES Act), the largest financial assistance bill to date, includes provisions to help small businesses. Fraudsters have already begun targeting small business owners during these economically difficult times. Be on the lookout for grant fraud, loan fraud, and phishing.
Individuals may receive fraudulent attempts through email asking them to click on links or attachments to complete an application for the program. Do not click on any links or attachments from unknown senders or unexpected correspondence.
Some emails may appear to come from a legitimate domain, so it is important to verify the validity of any requests asking for information. It is important to remember that any requests for US Cares Paycheck Protection Program will come directly from your financial institution. Disbursements will also only come from your bank.
Recognizing Phishing Emails
- Remain vigilant when opening emails from unknown senders. The email may appear to be from someone you know. Pay attention to grammatical errors.
- Never click any links or attachments in emails from someone you don’t know.
- Report suspicious emails with unknown attachments or links to your email provider.
- Ensure your personal computer systems and anti-virus are always up to date and running on the most current software version.
See sample phishing email below:
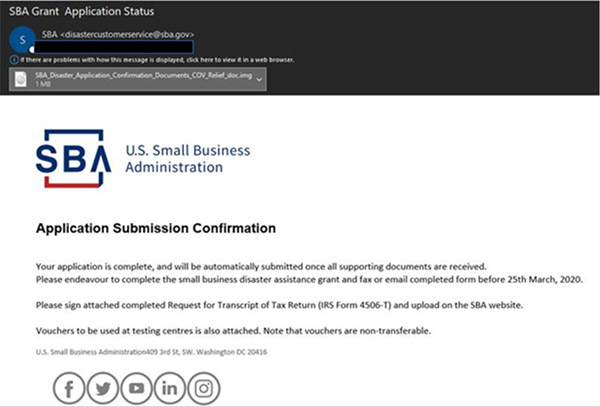
For more information and to report fraud attempts from the SBA please visit their website.
Please contact NBT Bank if you have provided any personal or financial information at 1-800-NBT-BANK or at reportfraud@nbtbank.com.
Business Email Compromise (BEC) Fraud continues to be popular
NBT Bank has recently noticed an increase in a type of fraud referred to as “Business Email Compromise or BEC”, and the way in which fraudsters are targeting businesses continues to change. Most often there is an attempt to get funds out the door via wire or ACH although other channels such as check could also be attempted.
Business Email Compromise (BEC) scams happen when an email account is compromised or spoofed, and an employee is convinced to wire money to a fraudster. The fraudster is able to fool an employee into submitting a wire transfer by posing as a supplier, vendor, co-worker, or business partner, and the email request may look like it is coming directly from your supplier, or may be part of an email chain you have had with your legitimate supplier in the past. When submitted, the transaction appears to be completely legitimate to the company's financial institution, and confirmation calls or other methods of verification may not be effective if verification is being made to the employee who submitted the request, as this employee believes they have been communicating with an established supplier or sales representative.
Always verify a request with a phone call to the individual who is sending it to you at a known number. Trust your gut! If something feels off about the communication; email signatures, grammar, spelling errors, request coming from someone who normally wouldn’t request this, etc. Don’t send any money without verifying.
How to protect yourself:
- Check to see if the request is consistent with how earlier wire payments have been made. Is your supplier asking you to wire funds to a new bank account or different location?
- Look carefully for small changes in email addresses that mimic legitimate email addresses. Do not rely on the display name shown, and always look for differences between the domain (@yahoo vs. @gmail) or sender name (ABCSupplies@ vs. ABCSupply@).
- Use an alternate method of communication to verify the identity of the person requesting the funds transfer. If the request is an email, then call and speak to the person using a known phone number to get a verbal confirmation for the request.
- Implement dual control approvals with your bank for wire transfer requests. If an employee submits a request for a wire transfer, have a different employee who is aware of Business Email Compromise and is willing to ask the right questions provide approval to your financial institution.
- Spread the word. Coach your employees about this type of fraud and the warning signs.
If you have any questions, please contact NBT Bank Cash Management Support at 1-800-NBT-Bank (628-2265), option 8.
Security Vulnerability Description:
The Federal Bureau of Investigation (FBI), Cybersecurity & Infrastructure Security Agency (CISA), and Health and Human Services (HHS) have released information detailing the rise of ransomware attacks. Common ransomware attacks have continuously been updated to become more effective.
These ransomware attacks have increased “the ease, speed, and profitability of victimization.” The FBI has found that ransomware attacks have increased for all industries. However, there is an even more dramatic increase in hospitals and the healthcare provider industry.
Risk Mitigation:
Network Best Practices
- Patch operating systems, software, and firmware as soon as manufacturers release updates.
- Check configurations for every operating system version for HPH organization-owned assets to prevent issues from arising that local users are unable to fix due to having local administration disabled
- Regularly change passwords to network systems and accounts and avoid reusing passwords for different accounts.
- Use multi-factor authentication where possible.
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs.
- Implement application and remote access to only allow systems to execute programs known ang permitted by the established security policy.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind.
- Audit logs to ensure new accounts are legitimate.
- Scan for open or listening ports and mediate those that are not needed.
- Identify critical assets such as patient database servers, medical records, and telehealth and telework infrastructure; create backups of these systems and house that backups offline from the network.
- Implement network segmentation. Sensitive data should not reside on the same server and network segment as the email environment.
- Set antivirus and anti-malware solutions to automatically update; conduct regular scams.
- Regularly backup all files offline.
Plans and Policies
It is recommended all businesses have an updated incident response plan in place to help ensure that the proper steps are taken if your company falls victim to a cyber-attack. Additionally, you can maintain an incident response retainer with a reliable cyber security company.
Ransomware Best Practices
The CISA, FBI and HHS does not recommend paying ransoms. Payment does not guarantee files will be recovered. It may also embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of ransomware, and/or fund illicit activities.
User Awareness Best Practices
It is important to continue to perform social engineering testing and training. Employees are the weakest link in terms of cyber security. It takes one person to click on a malicious link and download ransomware to your organization. Through continuous social engineering testing and training, the risk of human vulnerability can be reduced.
Resources to Prevent Increasing Ransomware Attacks
CISA’s National Cyber Awareness System
FBI Internet Crime Complaint Center
U.S. Secret Service (USSS) Preparing for a Cyber Incident
NIST Tips and Tactics for Dealing with Ransomware
Conference of State Bank Supervisors (CSBS)/USSS Ransomware Self-Assessment Tool
Business Email Compromise and Spear Phishing: A Sharp Cost
NBT Bank has recently noticed an increase in a type of fraud referred to as Business Email Compromise (BEC). This occurs when fraudsters fool an employee into submitting a wire transfer by posing as a supplier, vendor, or business partner. In a new variation of BEC, fraudsters are using spear phishing attempts. Spear phishing refers to targeted emails going to a specific department or line of business. For example, the accounting and finance department or payroll.
The email contains a link to what looks like an encrypted file. When clicked, the user is prompted for their username and password on a fake login screen. With this information, fraudsters can sort through their emails for invoices, communications with banks, or other important financial information. They also use this information to make rules in the user’s inbox to automatically forward emails for real time information. Most recently, there has been an increase in attacks toward healthcare, professional services, higher education and real estate closing companies.
How to protect yourself:
- Don’t click on links in suspicious emails. Clicking a link could compromise your account or your network.
- Check to see if the request is consistent with how earlier wire payments have been made. Is your supplier asking you to wire funds to a new bank account or different location?
- Look carefully for small changes in email addresses that mimic legitimate email addresses. Do not rely on the display name shown, and always look for differences between the domain (@yahoo vs. @gmail) or sender name (ABCSupplies@ vs. ABCSupply@).
- Use an alternate method of communication to verify. If the request is an email, then call and speak to the person using a known phone number to get a verbal confirmation for the request.
- Implement dual control approvals with your bank for wire transfer requests. If an employee submits a request for a wire transfer, have a different employee who is aware of BEC and is willing to ask the right questions and provide approval to your financial institution.
- Spread the word. Coach your employees about this type of fraud and the warning signs.
If you have any questions, please contact NBT Bank Cash Management Support at 800-NBT-Bank (628-2265), option 8.
Ransomware attacks continue to increase in frequency, and are becoming more sophisticated and targeted, meaning that an email containing an infected attachment can seem like it is coming from a trusted source such as a vendor or company. Malicious emails often no longer contain the typical indicators of phishing attempts, such as poor grammar and spelling, or "from" addresses which you do not recognize. It is extremely important to review all emails for content and purpose, and never open any attachments before verifying that the email is intended for you and is something which you were anticipating for a specific purpose.
What is Ransomware, and how does it happen to you? Ransomware attacks begin when an individual clicks on a malicious link or attachment in an email. Ransomware will then encrypt, or 'lock' all of the files on the user's computer, rendering the files unusable and inaccessible. After the files have been encrypted, the user will be prompted to pay a ransom to unlock their files.
Who is vulnerable? Ransomware attacks can be perpetrated against anyone, and caution must be practiced at all times.
How will you or your business be impacted?
If you fall victim to a Ransomware attack, the impact to individuals and businesses can reach far beyond removing the infection and recovering your files, and could also include:
- Temporary or permanent loss of sensitive or proprietary information. Your personal or business files could be temporarily inaccessible or lost forever.
- Disruption to regular operations. In the time it takes to respond to the attack, your computer files and the files on your network will be inaccessible, leaving your business inoperable or significantly impaired.
- Financial loss. In order to fully respond to and recover from this threat, you may be required to invest significant resources in repairing and restoring your device or network, whether it be through the use of an internal or external IT Professional, or in extreme cases where a lack of preparation has left you with no other option to recover your files, paying the ransom.
- Harm to an organization's reputation. Your business may suffer reputational harm when current customers or prospective clients learn that your business operations and their personal information have been affected by a Ransomware attack. Being prepared to appropriately prevent, detect, and respond to these events can help ensure a timely resumption of services and the protection of private customer information.
How to protect yourself: Prevent, Detect, Respond
- Keep your anti-virus software active and up to date. Your anti-virus software is only as good as your last update.
- Back up your files. Though creating a backup of your system will not prevent the execution of Ransomware, this preventative measure will allow for the recovery of data in an efficient and effective manner, without having to pay a ransom.
- Be wary of suspicious or unsolicited emails, especially those which contain attachments or links.
- Pay attention to anomalies when using your device, whether your computer seems to be running differently than usual, or if your computer is on a network of computers and seems to be communicating in a way in which it does not typically.
- Educate yourself on Ransomware by reading this and similar alerts, such as the one released by the United States Department of Homeland Security (DHS) and the Canadian Cyber Incident Response Center (CCIRC), which can be found by typing the following link into your web browser: https://www.us-cert.gov/ncas/alerts/.
- Paying the ransom is not recommended, and there is no guarantee the files will be decrypted upon paying the ransom. It is always recommended that victims work with an IT professional first before negotiating with the attackers.
For More information on Ransomware including an example of what a ransomware email might look like, please review our previous alert on Ransomware. It can be found by typing in the following web address into your browser:
https://www.nbtbank.com/Business/Customer-Support/Fraud-Information-Center/LatestFraudAlert/Ransomware
If you have any questions, please contact NBT Bank at 1-800-NBT-Bank (628-2265)

Nine Points of Protection

Latest Cyber Threats

Business Fraud Awareness, Prevention and Reporting Resources
Find out about resources available for businesses to prevent fraud, cybercrime and report incidents


